Can You Get Hacked by Replying to a Text? 5 Methods Your Phone Can Be Assessed

You might wonder—can you get hacked by replying to a text? The short answer is no—just replying won’t hack your phone.

However, hackers use sophisticated methods to gain access to devices. This article explores five ways hackers can exploit text messages to compromise your phone and how to protect yourself.
Can You Really Get Hacked by Replying to a Text?
The good news is that simply replying to a text won’t automatically give hackers access to your device. However, the real danger lies in what happens next.
Hackers often disguise their messages as legitimate communications from banks, delivery services, or even friends. These messages may contain malicious links that install spyware or direct you to fake websites designed to steal your credentials.
Additionally, some SMS attacks, such as "smishing" (SMS phishing), trick victims into revealing sensitive information like passwords or financial details.

Even if you don’t click on a link, responding to a scam text can confirm that your number is active, making you a target for future attacks.
To stay safe, avoid responding to unknown numbers, never click on suspicious links, and enable security features like spam filters and two-factor authentication (2FA).
Why You Might Want to Hack Someone’s Phone

When people hear the word "hack," they often think of cybercriminals stealing data or causing harm. However, hacking can also serve ethical and protective purposes, such as monitoring your loved ones' safety, ensuring responsible device usage, or retrieving lost information.
Here are some legitimate reasons why you might want to access someone’s phone ethically:
- Parental Monitoring
- Track their child's location in real time.
- Monitor text messages and social media interactions.
- Set screen time limits and restrict harmful apps.
- Protecting Elderly Family Members
- Ensure they don’t fall victim to digital fraud.
- Help locate them in case they wander off or get lost.
- Provide emergency assistance when needed.
- Recovering a Lost or Stolen Phone
- Locate the missing device.
- Lock or erase sensitive information remotely.
- Prevent identity theft if the phone falls into the wrong hands.
- Monitoring a Loved One’s Well-being
- Check their location to ensure they are safe.
- Noticing unusual behavior or distress signals in messages or social media activity.
- Offering timely help if they need support.
- Employee Monitoring for Security Purposes
- Ensure employees are using them for work-related activities.
- Protect sensitive company information from leaks.
- Locate lost or stolen corporate devices.
Parents want to keep their children safe from online predators, inappropriate content, and cyberbullying. Ethical phone monitoring apps help parents:
Older adults are often targets of scams, phishing attacks, and fraudulent calls. Ethical phone tracking can:
Losing a phone can be stressful, especially if it contains sensitive personal data. Ethical hacking techniques, such as GPS tracking and remote access tools, can help:
If a family member is struggling with mental health issues, or addiction, or is in an unsafe environment, ethical monitoring can provide peace of mind by:
Employers may need to track company-owned devices to:
Using legal and transparent tracking solutions, such as parental control apps or built-in phone tracking features, ensures that monitoring remains ethical and within the law.
5 Proven Methods to Hack Someone’s Device and View Texts
Hacking can help parents, caregivers, or employers ensure safety, protect sensitive data, and maintain accountability. Below are seven legitimate methods to monitor a loved one’s device and access text messages, along with their advantages and disadvantages.
1. Hack Devices and View Texts with SafeMyKid
One of the most effective ways to ensure digital safety is by using SafeMyKid, a trusted parental control app designed to help parents monitor their children’s online activity and protect them from potential cyber threats.

SafeMyKid offers advanced security features that detect suspicious messages, phishing scams, and other digital risks.
Scanning text messages and alerting parents to harmful content, provides a proactive way to safeguard children against cyberbullying, inappropriate conversations, and online predators.
Key Features of SafeMyKid Text Viewer
To help parents and guardians monitor text messages and protect their children from online threats, SafeMyKid offers advanced tracking and security features:
- Real-Time SMS Monitoring – Detects and alerts you about suspicious or harmful text messages.
- Call and App Monitoring – Blocks unauthorized numbers and tracks installed apps for potential risks.
- Keyword Alerts – Notifies parents if certain flagged words appear in messages.
- Remote Access Dashboard – Allows easy monitoring of texts and activity from any device.
- Screen Time Control – Limits texting and app usage to encourage healthy digital habits.
These features help ensure a safer texting experience while giving parents peace of mind.
How to Set Up SafeMyKid Text Viewer
To begin monitoring and securing text messages, follow these setup steps:
How to View Text Messages on Android Devices
Step 1. Sign up
Create an account on the SafeMyKid website.

Step 2. Download and Install the Android App
Get the SafeMyKid app. Follow on-screen instructions to allow necessary access for real-time monitoring.
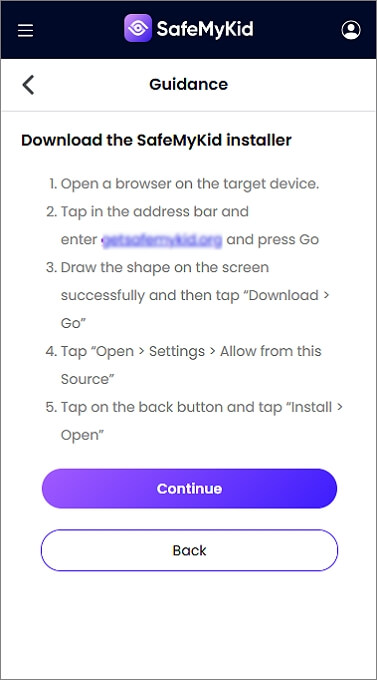
Step 3. View Text Messages on Android
Log into the SafeMyKid dashboard to view SMS activity and alerts.
How to View Text Messages on iPhone
Step 1. Sign Up
Register for a SafeMyKid account through the official site.

Step 2. Input iCloud Details
Provide the target device’s iCloud credentials for remote monitoring.
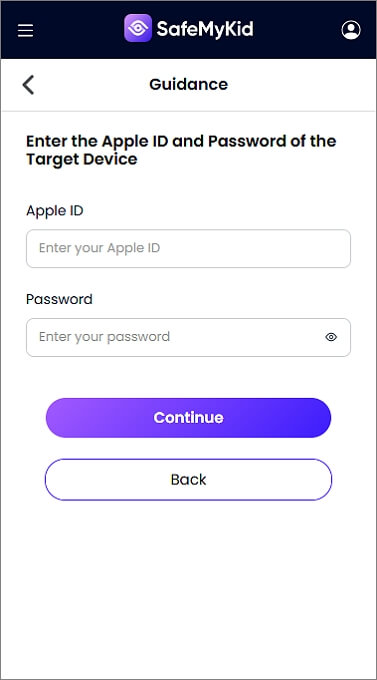
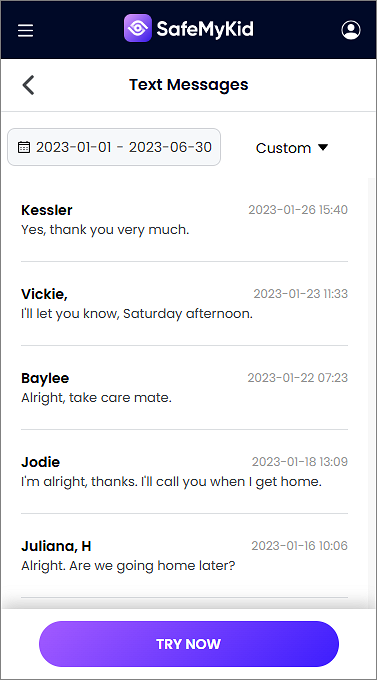
Step 3. Start Viewing Messages on iPhone Remotely
Log into your SafeMyKid dashboard to track messages without installing additional software.

With SafeMyKid, you can proactively prevent SMS scams and keep your personal information secure by monitoring suspicious messages and blocking potential threats.
This powerful tool helps detect phishing attempts, protects against malicious links, and ensures a safer digital environment for you and your family. Stay ahead of cyber threats with SafeMyKid.
2. iCloud Backup Monitoring (For iPhones with Access to Apple ID)
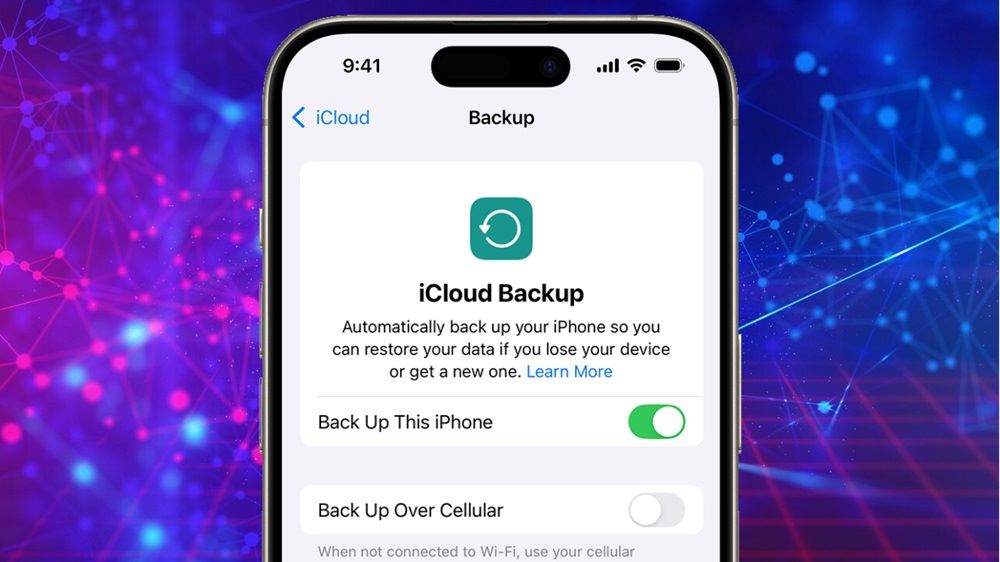
If the target device is an iPhone and you have access to the Apple ID and password, you can retrieve backups that contain messages, call history, and other data.
How It Works:
- Sign in to iCloud using the person's Apple ID on another device.
- Navigate to Backups to view stored messages and activity.
- Some monitoring apps also extract and display this data in a structured format.
Advantages:
- Free if you have access to Apple ID credentials
- Works remotely without needing the physical phone
Disadvantages:
- Requires Apple ID login credentials
- Does not provide real-time updates unless the device syncs frequently
3. Google Account Sync (For Android Devices with Shared Access)
Android devices linked to a Google account automatically sync messages, contacts, and location history, making it possible to retrieve text messages.
How It Works:
- Log into the linked Google account on another device.
- Check Google Messages or use a monitoring app that extracts synced data.
- View location history via Google Maps Timeline.
Advantages:
- Free and works remotely if the account is accessible
- No need for third-party apps
Disadvantages:
- Requires Google account login details
- Can be disabled by the device owner
4. SIM Card Cloning (For Advanced Users – Not Recommended for Unauthorized Use)

SIM cloning duplicates a person’s SIM card, allowing the clone to receive calls and texts sent to the original number. This method is complex and requires specialized hardware.
How It Works:
- Extract the IMSI (International Mobile Subscriber Identity) and authentication key from the SIM.
- Copy this data onto a blank SIM card.
- Insert the cloned SIM into another device to receive calls and texts.
Advantages:
- Allows real-time access to text messages and calls
- Works even if the original device is turned off
Disadvantages:
- Illegal without consent in most regions
- Requires technical expertise and SIM cloning tools
- Cannot monitor app-based messages (e.g., WhatsApp, Messenger)
5. Keylogger Software (For Capturing Keystrokes & Messages)

Keyloggers record everything typed on a device, including text messages, passwords, and search history. They are commonly used by parents and employers for security monitoring.
How It Works:
- Install a keylogger on the target device.
- The software logs every keystroke and sends reports to the monitoring account.
- Some keyloggers also capture screenshots of messages and activity.
Advantages:
- Captures all typed messages, even deleted ones
- Can track passwords and login details
Disadvantages:
- Requires installation on the device
- May be flagged as suspicious software
- Some features require payment
Popular Keyloggers: Spyrix, Refog, iKeyMonitor
6. SMS Forwarding & Call Monitoring (For Basic Text & Call Tracking)

Many phone carriers and monitoring apps allow you to set up text message forwarding, sending copies of received texts to another number or email.
How It Works:
- Set up SMS forwarding through the device’s settings (on Android) or using third-party apps.
- Forwarded messages are automatically sent to a designated number or email.
- Some apps also log call history and contacts.
Advantages:
- Easy to set up
- Works without additional software if carrier-supported
Disadvantages:
- Does not capture deleted messages
- Cannot track app-based messaging (e.g., WhatsApp, iMessage)
- Some services require payment
Popular Apps: SMS Forwarder, Call & SMS Tracker
7 Effective Ways to Stay Safe from Text Message Hacks
Hackers use deceptive text messages to trick users into revealing sensitive information or installing malware. To protect yourself, follow these essential precautions:
- Ignore and Delete Suspicious Messages
- Avoid Clicking on Links in Texts
- Enable Spam Filters and Message Blocking
- Be Cautious with OTP Requests
- Use Multi-Factor Authentication (MFA)
- Keep Your Phone and Apps Updated
- Verify Messages Before Taking Action
Never respond to unknown or strange texts, even if they seem urgent. Hackers use deceptive messages to trick you into revealing personal information or clicking malicious links. Deleting suspicious texts immediately reduces the risk of falling victim to scams or malware attacks.
Hackers use fraudulent links to install malware or steal personal data. Instead of clicking, verify the link by visiting the company’s official website or contacting customer support directly.
Even messages from known contacts can be compromised, so always double-check before taking action.
Most smartphones have built-in spam filters that detect and block suspicious messages. You can also manually block unknown or unwanted numbers to reduce scam attempts. Enabling these settings adds an extra layer of protection against phishing and malware-laden texts.
Never share one-time passwords (OTPs) with anyone, even if a message appears to be from your bank or a trusted company. Hackers often pose as legitimate services to trick you into revealing these codes, giving them access to your accounts. Always verify requests independently.
Enabling MFA adds an extra layer of security by requiring a second verification step, such as a fingerprint, authentication app, or security key. Even if hackers steal your password, they won’t be able to access your account without this additional authentication.
Regularly updating your phone’s operating system and apps ensures you have the latest security patches. Hackers often exploit outdated software to gain access to devices, so enabling automatic updates can help protect you from potential threats.
Scammers often impersonate banks, delivery services, or government agencies to trick you. If you receive an urgent text requesting sensitive information, contact the company directly using its official website or customer service number to confirm its legitimacy before responding.
Signs That Your Phone May Be Hacked

If your phone has been hacked, you might experience unusual behavior that indicates unauthorized access. Look out for the following warning signs:
- Battery Draining Faster Than Usual – Malware running in the background can consume power rapidly.
- Unfamiliar Apps Installed Without Permission – Hackers may install spyware or malicious apps to monitor your activity.
- Strange Messages Sent from Your Phone – If your contacts receive messages you didn’t send, your device might be compromised.
- Increased Data Usage – Malware or spyware can send stolen data to hackers, leading to a spike in data consumption.
- Unexpected Pop-ups or Redirects While Browsing – Frequent ads or browser redirections can indicate adware or malware infection.
If you notice any of these signs, take immediate action to secure your phone and prevent further damage.
FAQs on Being Hacked by Replying to a Text
To help you better understand text message security risks, here are some frequently asked questions:
1. How do scammers get my phone number in the first place?
Scammers obtain phone numbers through data breaches, leaked contact lists, social media, or by generating random numbers using automated systems. Some even buy bulk phone numbers from illegal sources on the dark web.
2. Can a scam text infect my phone just by opening it?
No, simply opening a text message won’t infect your phone. However, if the message contains an infected attachment, a malicious link, or exploits a rare vulnerability, it could lead to security risks.
3. Is it safe to block or report scam numbers?
Yes, blocking scam numbers prevents future messages from the same sender. Reporting the number to your mobile carrier or spam-reporting services helps track and prevent fraud. However, scammers often change numbers frequently.
4. Can I recover money lost from an SMS scam?
It depends on how you were scammed. If you provided financial details or made a payment, immediately contact your bank and report fraud. Some banks may reverse transactions, but success depends on the situation and speed of reporting.
5. What should I do if I receive a scam text on my business or work phone?
Do not engage with the message. Report it to your company’s IT security team and follow any corporate security guidelines to prevent breaches. Business devices are often targeted for phishing scams.
6. Are iPhones safer from SMS scams than Android devices?
iPhones have stronger built-in security features, such as iMessage filtering and app sandboxing, but they are not immune. iPhones can still be vulnerable to phishing scams, social engineering, and rare zero-click exploits.
Conclusion
Can you get hacked by replying to a text? Simply replying to a text won’t hack your phone. You should use SafeMyKid to monitor texts for any suspicious activity.
By using SafeMyKid, you can protect the phone, data, and personal information of your loved ones from cyber threats. Stay safe, stay aware, and always think before you tap!