How to Hack an iPhone: 5 Secrets Hackers Won’t Tell You

If you’re searching for how to hack an iPhone, you’re probably dealing with a serious problem. Maybe you’re a concerned parent worried about your child’s online activity. Maybe you suspect your partner is hiding something. Or perhaps you lost access to your own device and need a way back in.
While Apple designs iOS to be secure, hackers and tech enthusiasts have found multiple ways to bypass restrictions, break into locked devices, and extract information.
This guide cuts through the noise and lays out five real methods you can use to break into iPhones. Whether you're looking for a way in or just curious about how it works, here’s everything you need to know.

Why You Might Need to Hack Someone’s iPhone
While Apple has built strong security measures to protect user privacy, certain circumstances justify the need to access an iPhone. Below are some situations where hacking an iPhone is crucial:
Parental Monitoring and Child Safety
Children frequently use social media platforms with disappearing messages and hidden features, making it difficult for parents to track their interactions. Monitoring their iPhone usage helps ensure they engage responsibly and stay protected from online threats.
Investigating Infidelity and Relationship Concerns
Secrecy, such as hiding screens or frequently changing passwords, can create doubts in relationships. While open communication is ideal, some seek verification by checking for hidden chats, deleted messages, or suspicious activity before addressing concerns.
Recovering a Locked or Lost iPhone
Forgotten passwords, multiple incorrect attempts, or iCloud recovery issues can lock users out of their own iPhones. In such cases, accessing the device becomes essential for restoring data and regaining control.
Employee Monitoring and Data Protection
Companies issuing iPhones for work purposes need to ensure employees use them professionally. Monitoring these devices can help prevent data leaks, detect misuse, and safeguard confidential business information.
Preventing Elderly Scams and Financial Exploitation
Senior citizens may unknowingly fall victim to phishing scams or fraudulent transactions. Family members may need to access their devices to protect them from digital threats and unauthorized financial activity.
The Best Way on How to Hack an iPhone

If you're looking for an easy, effective way to hack an iPhone, SafeMyKid offers a powerful monitoring tool that allows you to discreetly access an iPhone’s messages, calls, location, social media, and more. Unlike complex hacking methods, this app requires no coding knowledge or technical skills.
Key Features of SafeMyKid
SafeMyKid operates privately, making it invisible to the user while collecting real-time data. It’s often used by parents, employers, and investigators to track and monitor iPhone activity. Below are some key features of SafeMyKid:
- Stealth Mode – Runs invisibly in the background without detection.
- Text Message & Call Log Tracking – Monitor incoming and outgoing calls and messages, even deleted ones.
- GPS Location Tracking – Track real-time locations and view history logs.
- Social Media Monitoring – View messages and activity on WhatsApp, Instagram, Snapchat, and other apps.
- Browser History & Website Blocking – See browsing activity, even if the history is deleted, and block harmful websites.
- Keylogger Feature – Capture every keystroke typed on the device, including search queries and passwords.
- Camera & Microphone Access – Detect unauthorized use of your device’s camera and microphone.
How to Set Up SafeMyKid to Hack an iPhone
Setting up SafeMyKid is simple and takes just a few minutes.
Step 1. Sign Up & Create an Account
Visit the SafeMyKid website and create an account using your email. Choose a subscription plan that suits your needs.

Step 2. Setup SafeMyKid on the Target iPhone
For iPhones, there’s no need to install any apps. Simply log in with the target phone’s iCloud credentials to get started with hacking.
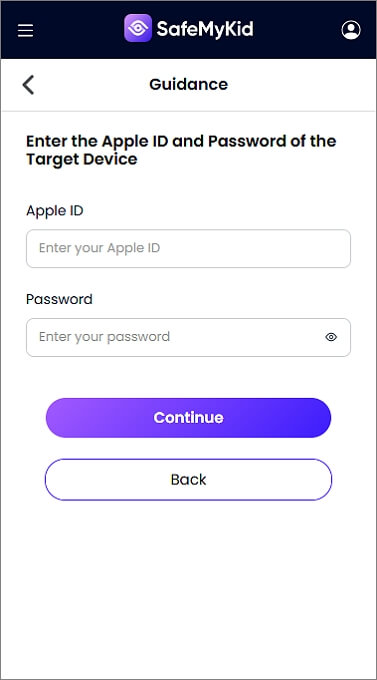
Step 3. How to Hack an iPhone
Once the setup is complete, log into your SafeMyKid dashboard from any device. The dashboard will give you access to the real-time GPS location, incoming and outgoing calls, text messages, and more.
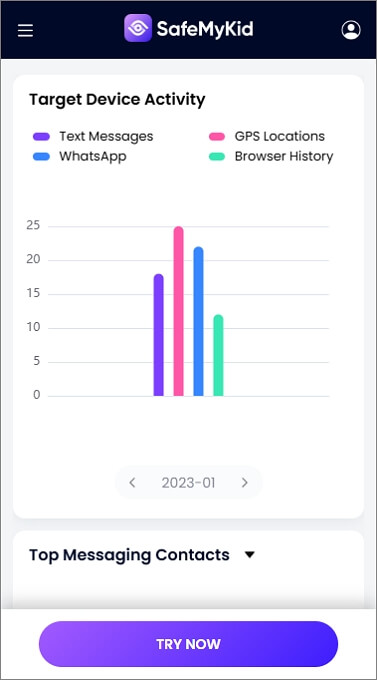
5 Other Ways to Hack an iPhone Easily

Apple's security may be strong, but no system is unbreakable. These five iPhone hacking techniques expose the weaknesses you need to know.
1. Remote Hacking via Apple ID (No Clicks Required!)

One of the easiest ways to hack an iPhone without touching it is through the Apple ID. If you have access to someone’s Apple ID credentials, you can remotely break into their iPhone and retrieve almost everything stored on the device.
This method is commonly used by hackers, investigators, and even law enforcement to extract data from an iPhone. Since Apple’s ecosystem relies heavily on iCloud, accessing an Apple ID gives you control over:
- Text messages and iMessages – Read all incoming and outgoing conversations.
- Call logs – Check who they’ve been calling and for how long.
- Photos and videos – View media stored in iCloud, even deleted files.
- Emails and social media accounts – Gain access if they use iCloud Keychain to save passwords.
- Live location tracking – Track the iPhone’s real-time location using Find My iPhone.
How to Hack an iPhone Using Apple ID
- Obtain the Apple ID credentials – This could be done through phishing attacks, social engineering, or if the person has shared their login details with you before.
- Log into iCloud.com – Enter the Apple ID and password to access synced data, including messages, emails, and locations.
- Use ‘Find My iPhone’ – You can track the device, lock it, or even erase all data remotely.
- Retrieve iCloud backups – Download full backups from iCloud to restore and extract more data from the target iPhone.
Limitations:
- Two-Factor Authentication (2FA) – If enabled, you need access to the user’s secondary device or phone number to bypass the security check.
- Apple’s Security Alerts – Apple sends security notifications to the account owner when a login occurs from an unfamiliar device, raising suspicion.
- Limited Access to Encrypted Data – Some sensitive iPhone data, like certain keychain passwords, is encrypted and not included in iCloud backups.
- Remote Locking & Wiping – If the user detects unauthorized access, they can remotely log out or erase their iPhone to cut off further data exposure.
2. iMessage Exploits That Require No Interaction
Hackers have discovered vulnerabilities in Apple’s iMessage service that allow them to send a specially crafted message that, once received, can take over the device without the user even opening it. These exploits are known as zero-click attacks, meaning they don’t require any action from the victim.
How to Hack an iPhone Using iMessage Exploits
- Find an iMessage vulnerability – Some older iOS versions have critical flaws that you can exploit to gain remote access.
- Send a malicious iMessage – Craft a special iMessage with a hidden code and send it to the target’s phone number or Apple ID.
- Trigger the exploit – Once the message is received, the malicious code executes automatically, granting you access to system files, messages, and even the microphone and camera.
- Extract sensitive data – you can now access photos, contacts, emails, and other stored information.
Limitations:
- Requires a known vulnerability – Apple frequently patches these exploits with security updates, making this method unreliable over time.
- High-level technical skill needed – Zero-click exploits are complex and typically require advanced cybersecurity expertise to execute.
- Limited attack window – If a user updates their iOS regularly, the chances of this method succeeding decrease significantly.
- Detection by Apple security – Apple actively investigates and blocks iMessage-based attacks, reducing the effectiveness of long-term exploitation.
3. Safari & iCloud Exploits That Steal Your Data

Since Safari is Apple’s default browser, a security flaw in it can expose sensitive data. Similarly, iCloud syncs personal data across devices, making it a prime target for hackers who want access to messages, photos, and even passwords.
How to Hack an iPhone Using Safari & iCloud Exploits
- Find a Safari vulnerability – Hackers discover flaws in the Safari browser that allow them to inject malicious scripts into a website.
- Trick the target into visiting a hacked website – When the iPhone user visits the site, the hidden script runs in the background, extracting data or executing commands.
- Steal iCloud login credentials – If the hacker manages to compromise the Safari autofill system, they can retrieve saved passwords, including the Apple ID credentials.
- Access iCloud backups – With the Apple ID credentials, the hacker can log into iCloud.com and download backups containing photos, contacts, and messages.
Limitations:
- Requires user interaction – The victim must visit a compromised website for the exploit to work.
- Apple’s sandboxing limits damage – Safari runs web processes in a sandbox, limiting what an attacker can do with a single exploit.
- Frequent security patches – Apple fixes browser vulnerabilities quickly, making long-term exploitation difficult.
- Encrypted keychain protection – Even if hackers steal iCloud credentials, many stored passwords require an additional authentication step.
4. Public Wi-Fi Attacks That Expose Your iPhone

One of the easiest ways to hack an iPhone without physical access is through public Wi-Fi attacks. Many iPhone users connect to free Wi-Fi networks at cafes, airports, and hotels without realizing they could be exposing their private data to hackers.
You can set up fake Wi-Fi networks or use man-in-the-middle (MITM) attacks to intercept all data sent and received by the iPhone. This includes login credentials, messages, emails, and even banking details.
How to Hack an iPhone Using Public Wi-Fi Attacks:
- Create a fake Wi-Fi hotspot – Start by setting up a free Wi-Fi network with a legitimate-sounding name like “Airport Free Wi-Fi” or “Starbucks Guest.”
- Wait for victims to connect – When an iPhone user connects, you can gain access to their internet traffic.
- Intercept login credentials – Using packet-sniffing tools, you can capture usernames, passwords, and session cookies.
- Redirect the user to fake login pages – You can force users to log into fake versions of social media, email, or bank websites, getting their credentials in real-time.
- Monitor browsing activity – You can track which websites the user visits and extract sensitive information.
Limitations:
- HTTPS encryption blocks most attacks – Secure websites (with HTTPS) encrypt traffic, making it much harder to steal login data.
- Requires the victim to connect willingly – Users who are cautious about Wi-Fi security won’t fall for this attack.
- Limited access to device files – MITM attacks can steal login credentials but do not provide direct access to files stored on the iPhone.
- Apple’s vpn & Private Relay – iPhones with iCloud Private Relay or VPNs encrypt traffic, reducing the effectiveness of this method.
5. Spyware & Tracking Apps Used to Monitor You
Another common way to hack an iPhone is by installing spyware or tracking apps on the target device. These apps are often marketed as parental monitoring tools but can also be used to secretly track someone’s phone activity.
Once installed, spyware runs silently in the background, recording every action taken on the iPhone, including text messages, call logs, GPS location, and even keystrokes.
How to Hack an iPhone Using Spyware & Tracking Apps
- Gain temporary access to the iPhone – Physical access for a few minutes is needed to install the spyware. Some advanced versions allow remote installation if the iCloud credentials are known.
- Install a spy app – Popular tracking apps like mSpy, FlexiSPY, and SafeMyKid allow complete monitoring of an iPhone’s activity.
- Enable stealth mode – Once activated, the app hides itself from the home screen, making it undetectable to the victim.
- Monitor everything remotely – The hacker can now log into the spyware dashboard from any device and see:
- Text messages and iMessages (including deleted ones)
- Call logs and contacts
- GPS location and movement history
- Social media activity (WhatsApp, Instagram, Snapchat, etc.)
- Web browsing history and keystrokes
- Use keylogging to steal passwords – Some spyware apps include a keylogger that records everything typed, including passwords for email, banking, and social media accounts.
Limitations:
- Physical access is usually required – Most spyware needs to be manually installed on the target iPhone, requiring at least a few minutes of physical access to the device.
- iPhones with strong security can't install spyware easily – Unless the iPhone is jailbroken, installing third-party tracking apps is difficult due to Apple’s strict App Store policies.
- Spyware can be detected & removed – Many security apps and Apple’s iOS updates can detect and remove unauthorized tracking software. Additionally, resetting the iPhone wipes spyware completely.
- Apple’s security updates reduce effectiveness – Spyware developers rely on security loopholes, but frequent iOS updates patch these vulnerabilities, making spyware less effective over time.
- Legal consequences – Installing spyware without explicit consent is illegal in many countries and could lead to severe legal action if discovered.
5 Signs Your iPhone Might Be Hacked
Think your iPhone has been compromised? Here are key warning signs and what to do about them.
| Warning Sign | What It Means | How to Fix It |
|---|---|---|
| Battery Drains Fast | Hidden spyware or background processes are running. | Check battery usage in settings & delete unknown apps. |
| Phone Overheats Frequently | Malware or unauthorized apps may be active. | Restart your device & update iOS. |
| Unusual Data Usage | Spyware or remote access tools might be transmitting data. | Monitor data usage & reset network settings. |
| Pop-ups or Strange Messages | Possible phishing attempts or malware infection. | Don’t click suspicious links & scan for malware. |
| Random Apps Appear | Your iPhone may have been jailbroken remotely. | Remove unknown apps & reset to factory settings. |
FAQs about iPhone Hacking and Protecting Your Device
You’ve learned how iPhones get hacked—now let’s clear up some of the biggest questions and misconceptions about iPhone hacking.
1. Can hackers really break into an iPhone remotely?
Yes, hackers can exploit vulnerabilities to gain remote access to an iPhone without physical contact. Some attacks require only an Apple ID, while others take advantage of iMessage or Safari flaws.
2. What is CVE-2019-8641, and is my iPhone still at risk?
CVE-2019-8641 was a major security flaw that allowed hackers to remotely control an iPhone using just the Apple ID. Apple has since patched this issue, but if your device is not updated, you may still be vulnerable.
3. How do hackers use iMessage to break into an iPhone?
Hackers can send a specially crafted iMessage that exploits security flaws, giving them access to data or even control over the device—without the user clicking anything.
4. Can hackers spy on my iPhone camera or microphone?
Yes, some exploits allow hackers to remotely activate an iPhone’s camera or microphone without the owner knowing. This can be used for spying or recording conversations.
5. How can I protect my iPhone from being hacked?
Always update to the latest iOS version, enable two-factor authentication, avoid public Wi-Fi, disable iMessage if not needed, and use security tools like SafeMyKid to monitor suspicious activity.
Final Thoughts
While iPhones are designed with some of the most advanced security features, they are not invincible. With the right understanding of how to hack an iPhone, gaining access to an iPhone’s messages, calls, location, and private data is entirely possible.
Some hacking methods require technical expertise, while others, like spyware or Apple ID-based access, make it shockingly simple to retrieve sensitive information.
If you need a straightforward and effective solution, tools like SafeMyKid eliminate the guesswork, giving you direct access to an iPhone’s data in real-time, without detection.



