iCloud Hack: 5 Ways It Happens and What to Do

Understanding iCloud hack is crucial in today’s digital age, where data breaches and unauthorized access are growing concerns. While unethical hacking can lead to severe privacy violations, it is equally important to study these vulnerabilities.

In this article, we’ll explore methods for assessing iCloud security, highlighting responsible hacking techniques and best practices to safeguard data from cyber threats.
Why Someone Might Need to Carry Out an iCloud Hack?
While hacking is often associated with illegal activities, there are ethical reasons why someone might need to access an iCloud account. Ethical iCloud hacking is typically done with consent or for protective purposes, ensuring safety, security, and accountability in various situations.

Here are some legitimate reasons why iCloud access may be necessary:
- Parental Monitoring
- Ensure they are not engaging in unsafe online activities.
- Track their location for safety purposes.
- Prevent exposure to harmful content or dangerous individuals.
- Recovering a Lost or Forgotten Password
- Accessing a Deceased Loved One’s Account
- Spousal Monitoring
- Cybersecurity Research & Ethical Hacking
- Preventing cybercriminals from exploiting weaknesses.
- Educating users on better security practices.
- Strengthening iCloud’s overall security measures.
In today's digital world, children are exposed to various online threats, including cyberbullying, inappropriate content, and online predators. Parents may need to monitor their child’s iCloud account to:
Ethical parental monitoring should be done with transparency and proper communication to maintain trust between parents and children.
Losing access to an iCloud account can be frustrating, especially when critical files, photos, or documents are stored in the cloud. Ethical hacking techniques, such as retrieving security questions or using authorized tools, can help regain access when conventional recovery methods fail.
When a loved one passes away, family members may need to access their iCloud account to retrieve important documents, photos, or financial records. Apple has strict policies regarding account access after death, so ethical hacking methods may sometimes be necessary when legal procedures take too long.
In relationships where trust issues arise or safety is a concern, some partners may agree to share iCloud access for transparency. This could be useful in cases of suspected infidelity, financial dishonesty, or even protection against abusive situations.
Cybersecurity professionals and ethical hackers study iCloud vulnerabilities to identify security flaws and help improve Apple’s security systems. This type of ethical hacking is essential for:
5 Proven Ways to Carry Out an iCloud Hack
Ethical iCloud hacking involves gaining access to an iCloud account for legitimate and justified reasons, such as parental monitoring, account recovery, cybersecurity research, or accessing a deceased loved one’s data.
Unlike malicious hacking, ethical methods rely on legal and authorized approaches that do not violate privacy laws. Here’s how an ethical iCloud hack might happen:
1. Effortlessly Monitor iCloud with SafeMyKid
SafeMyKid is an advanced parental control tool that helps monitor your child's iCloud activity without direct access to their device. It provides a seamless way to track messages, call logs, browsing history, location, and app usage through a secure online dashboard.
With real-time updates and stealth mode operation, SafeMyKid ensures discreet monitoring while prioritizing child safety. Additionally, it offers alerts for suspicious activities, helping parents take proactive steps to protect their children from online threats.
Whether you need to monitor screen time, set restrictions, or review multimedia files, SafeMyKid delivers a comprehensive and user-friendly solution.

Key Features of SafeMyKid iCloud Hacker
SafeMyKid iCloud hacker provides a powerful and discreet way to monitor iCloud activity, ensuring parental control and security without direct device access. Designed for ease of use, it helps parents stay informed about their child’s digital interactions while maintaining privacy and safety.
It offers features like:
- Activity Monitoring – Track messages, call logs, browsing history, and app usage remotely.
- Location Tracking – Access real-time GPS updates and review location history to ensure your child's safety.
- Real-Time Alerts – Receive instant notifications for suspicious activities, unauthorized logins, or inappropriate content.
- Stealth Mode – Operates discreetly in the background without detection.
- iCloud Data Access – Syncs with iCloud backups to retrieve photos, videos, notes, and other stored data.
How to Use SafeMyKid iCloud Hacker
Getting started with SafeMyKid iCloud Hacker is simple and requires no physical access to the target device. By securely syncing with iCloud, you can discreetly monitor activity without detection.
Step 1. Sign Up
Create an account on SafeMyKid’s official website.

Step 2. Sync iCloud
Input the target iPhone’s iCloud credentials to enable remote access.
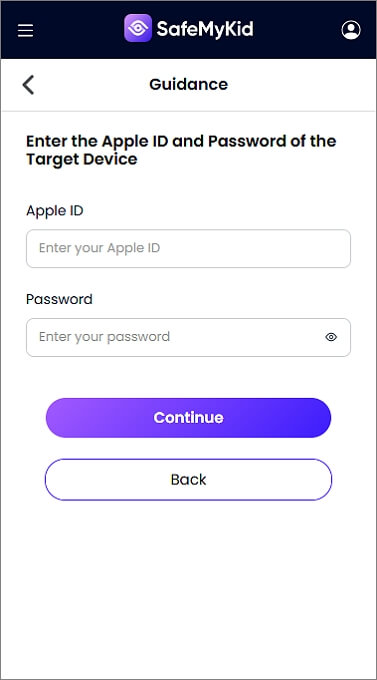
Step 3. Hack iCloud on iPhone
View iCloud data, including messages, call logs, location history, and more, through the SafeMyKid dashboard.
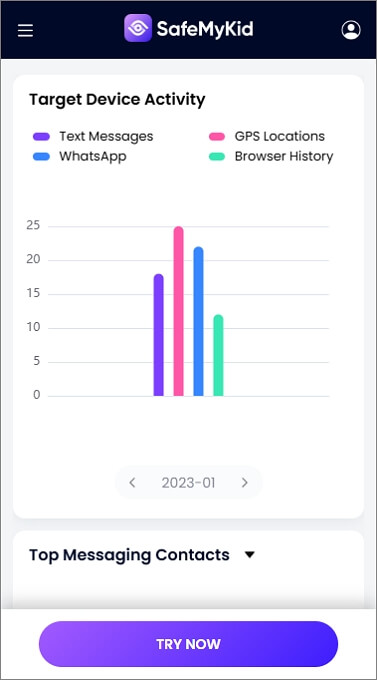
Reasons to Recommend SafeMyKid iCloud Hacker:
SafeMyKid iCloud hacker stands out as the ultimate monitoring solution for parents and spouses who need a discreet and reliable way to track iCloud activity. Unlike other apps that require complex installations or physical access to the target device, SafeMyKid offers a seamless setup—simply log in with iCloud credentials, and you're ready to monitor remotely.
With its comprehensive features, you can track messages, call logs, app usage, location history, and even receive real-time alerts for suspicious activities. What sets SafeMyKid apart is its strong commitment to privacy and security, ensuring that all monitored data remains protected and confidential.
Whether you're a parent concerned about your child’s online safety or a spouse seeking clarity, SafeMyKid provides a trustworthy, hassle-free, and effective solution over other tracking apps.
2. Using Apple’s Account Recovery Methods
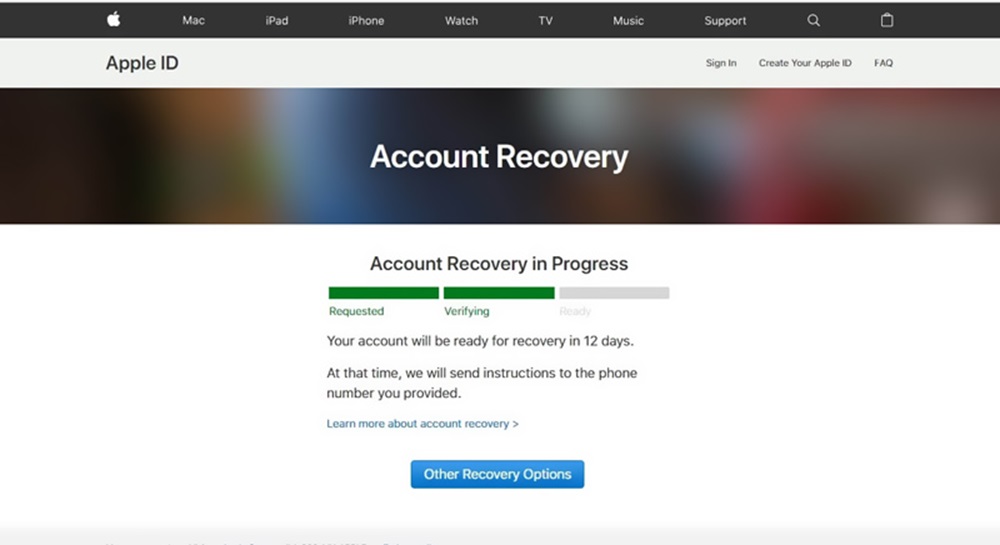
Apple provides built-in ways to regain access to an iCloud account, making hacking unnecessary in most cases. These methods include:
- Forgot Password Option: If you have access to the registered email or phone number, you can reset the password through Apple’s official recovery page.
- Two-Factor Authentication (2FA): If 2FA is enabled, access can be granted by approving the request on a trusted device.
- Security Questions: Answering the account’s security questions correctly can provide access.
This method is useful when accessing a lost account or retrieving information for a deceased loved one.
3. Using Family Sharing for Parental Monitoring
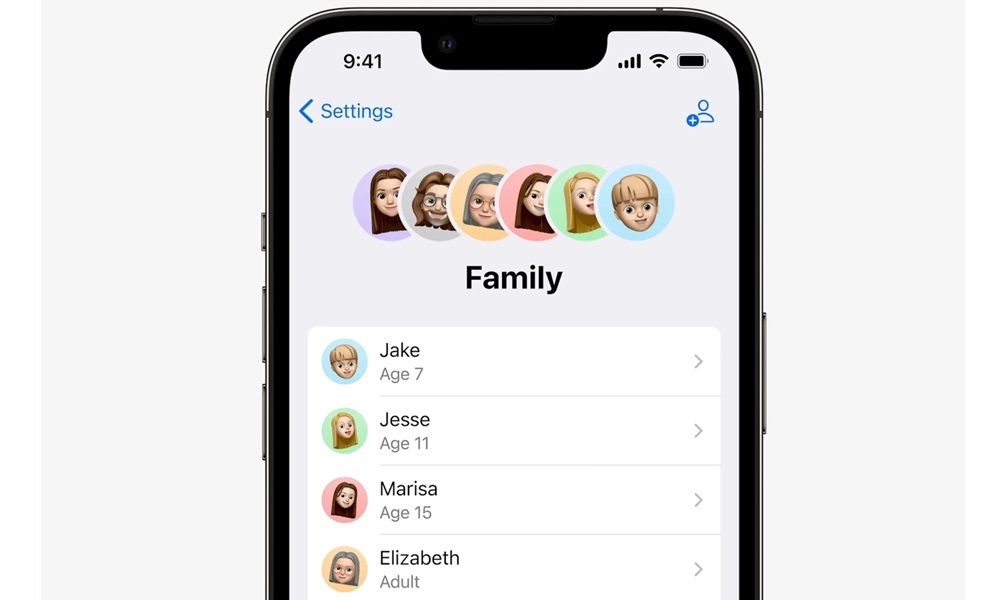
Apple’s Family Sharing feature allows parents to monitor their child’s iCloud activities ethically. With Family Sharing, parents can:
- View their child’s location in real-time.
- Approve or decline app downloads.
- Monitor purchases and subscriptions.
- Set screen time limits.
Instead of hacking, this is an Apple-approved way to ethically monitor a child's digital activities.
4. Accessing iCloud Backups via Authorized Devices
If someone has a legitimate reason to access an iCloud account, they can do so through a trusted device linked to the account.
- When an iPhone, iPad, or Mac is logged into an iCloud account, the data (photos, messages, notes, etc.) is automatically synced.
- A parent, spouse (with consent), or family member with access to a shared device can retrieve data from iCloud without illegal hacking.
This method is particularly useful for digital forensics experts working on cybersecurity cases or ethical investigations.
5. Ethical Cybersecurity Testing (Penetration Testing)

Cybersecurity experts conduct ethical hacking (also known as penetration testing) to identify weaknesses in iCloud’s security.
- They use specialized software tools to simulate cyberattacks and analyze vulnerabilities.
- Apple encourages ethical hackers to report security flaws through the Apple Security Bounty Program, which rewards researchers for discovering and reporting security issues.
This approach helps improve overall iCloud security while ensuring users’ data remains protected.
What to Do If Your iCloud Is Hacked
Discovering that your iCloud account has been hacked can be alarming, but taking immediate action can help prevent further damage. Hackers can access sensitive data, including personal photos, messages, and even payment details, so it's crucial to act fast to regain control.

Immediate Steps to Take:
- Change Your Password:
Immediately update your Apple ID password to prevent further unauthorized access. Go to Settings > Apple ID > Password & Security and create a strong, unique password. Avoid using easily guessable combinations like birthdays or common words. - Revoke Unauthorized Access:
Check your iCloud-connected devices and remove any unfamiliar ones. On your iPhone, go to Settings > Apple ID > Devices, and on your Mac, visit System Preferences > Apple ID to ensure only trusted devices are linked to your account. - Enable Two-Factor Authentication (2FA):
If you haven’t already, turn on 2FA to add an extra layer of security. This feature requires a verification code from a trusted device before granting access, making it harder for hackers to log in. - Review Account Activity:
Log in to appleid.apple.com and check recent activity. Look for unrecognized logins, changed recovery information, or unauthorized purchases. If you see suspicious transactions, report them immediately. - Contact Apple Support:
If you believe your account has been compromised beyond your control, reach out to Apple Support for assistance. They can help secure your account, restore lost data, and guide you through further recovery steps.
Why Act Quickly?
The faster you take action, the less likely hackers can exploit your data. Delays may allow them to lock you out completely, steal personal information, or use your iCloud credentials for fraudulent activities. By securing your account promptly, you can prevent identity theft, financial loss, and further breaches of privacy.
FAQs about Preventing an iCloud Hack
When it comes to securing your iCloud account, many users have common concerns about potential threats and best practices for protection. Below are some frequently asked questions to help you safeguard your data and prevent unauthorized access.
1. Can someone hack my iCloud without knowing my password?
Yes, hackers can use phishing scams, SIM swapping, or malware to gain access to your iCloud account without directly knowing your password. This is why enabling two-factor authentication (2FA) and monitoring account activity is crucial.
2. How can I check if my iCloud account has been compromised?
You can check for unusual activity by reviewing the devices logged into your iCloud account. Go to "Settings" > "Apple ID" > "Devices" to see if there are any unrecognized logins. Additionally, Apple will notify you of suspicious login attempts via email.
3. Does Apple provide any official tools to recover a hacked iCloud account?
Yes, Apple allows users to recover their accounts through the "Forgot Password" option or via Apple Support. If you believe your account has been hacked, you should immediately reset your password and remove any unauthorized devices linked to your iCloud.
4. Can I use SafeMyKid to monitor my iCloud without physical access to the device?
Yes, SafeMyKid allows users to monitor iCloud activity remotely without requiring physical access to the target iPhone. You simply need to sync the iCloud credentials with the SafeMyKid dashboard to track messages, locations, and other relevant data.
5. How often should I change my Apple ID password for better security?
It is recommended to change your Apple ID password every few months, especially if you suspect any suspicious activity or if your credentials were involved in a data breach. Using a password manager can help you create and store strong passwords securely.
6. What should I do if I receive a suspicious email claiming to be from Apple?
Do not click on any links or enter your credentials. Instead, check the sender’s email address carefully, as phishing emails often come from unofficial domains. If you are unsure, go directly to Apple's official website and log in from there. You can also report phishing attempts to Apple by forwarding the email to [email protected].
Conclusion
To carry out an iCloud hack you need to use responsible methods that prioritize security, privacy, and consent. Tools like SafeMyKid provide a legitimate way to monitor iCloud activity, helping parents or authorized users ensure data safety without violating ethical boundaries.
By following these five proven ways, you can securely access or recover an iCloud account when necessary, while also protecting sensitive information from unauthorized breaches.


