How to Install Spyware via Text Message for Free: Advanced and Common Methods

Can you install spyware via text message for free? The idea of remotely spying on a phone using just a text might sound like something from a spy movie, but the reality is that it is possible.

If you want to monitor someone’s phone activities, there are 8 ways to install spyware via text message for both Android and iPhone. Let’s dive into how these work.
Is It Possible to Install Spyware via Text Message?
Yes, but it’s not as simple as just sending a message and gaining instant access. Both Android and iPhone have built-in security features that prevent unauthorized installations.
However, hackers and advanced monitoring software developers have found ways to bypass these defenses.
Here’s what you need to know about spyware installation via text message:
- Android devices are more vulnerable because they allow the installation of apps from third-party sources.
- iPhones have stronger protections, but security flaws in apps like iMessage can be exploited.
- User interaction is often required—meaning the target must click a link, download an attachment, or install an app unknowingly.
- Zero-click attacks exist but are rare and require highly advanced spyware tools.
Now, let’s explore the ways to install spyware via text message for free and how they work.
Best Phone Spyware Solution: SafeMyKid
Instead of relying on risky and unreliable methods to install spyware via text message, the safest and most effective way to monitor an Android device or iOS device is by using SafeMyKid.
This advanced monitoring tool offers stealth mode operation, real-time tracking, and comprehensive monitoring features without detection. With SafeMyKid, you can remotely access calls, messages, GPS location, and social media activity in a secure and legal manner.

Why Choose SafeMyKid Phone Spyware Solution?
If you're looking for a comprehensive and discreet monitoring solution, SafeMyKid offers a range of features designed to keep you informed without being intrusive. Here’s why it’s the ideal spyware solution:
- Stealth Mode– Operates silently in the background, ensuring no detection by the target.
- Full Monitoring– Tracks calls, messages, GPS location, and social media activity to provide a complete picture.
- Remote Access– Once set up, you can monitor all activities remotely without needing to interact directly with the target device.
- Real-Time Alerts– Get instant notifications when specific activities are detected, such as location changes or social media activity.
- Keylogger Feature– Monitors keystrokes to see what is being typed in messages, search engines, and social apps.
- App Activity Monitoring– Tracks the usage of apps on the device, including times and interactions within apps.
- GPS Tracking & Geofencing– Receive live location updates and set alerts for when the device enters or exits a predefined area.
- Multimedia Monitoring– View photos, videos, and voice messages stored on the device to ensure no inappropriate content is shared.
- Access to Browsing History– Monitor all internet activity, including websites visited and search terms used, to keep track of online behavior.
SafeMyKid combines convenience, power, and discretion, providing you with peace of mind while ensuring complete privacy protection for those under your care.
How to Use SafeMyKid Phone Spyware
Setting up SafeMyKid is simple and efficient, with a streamlined process for both Android and iPhone devices. Here's how to get started:
How to Use SafeMyKid Spyware on Android
Step 1. Sign up
Create a SafeMyKid account by visiting their website and providing the necessary information.

Step 2. Download and Install The App
Download the SafeMyKid app on the target Android phone from the official website or Google Play Store. Follow the on-screen instructions to install the app.
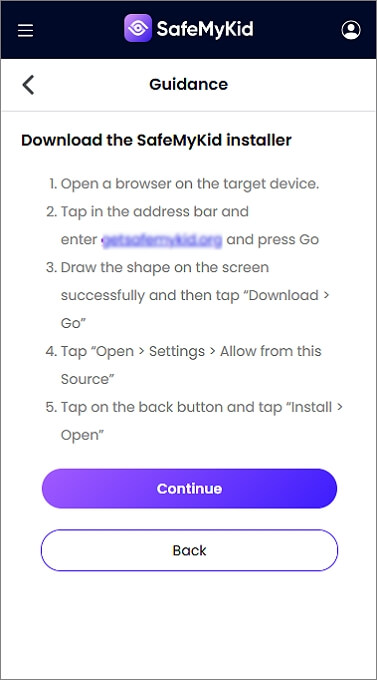
Step 3. Begin to Spy on Android
Once installed, grant necessary permissions, and then monitor the device remotely through the SafeMyKid web dashboard. You can track location, messages, calls, and social media interactions.
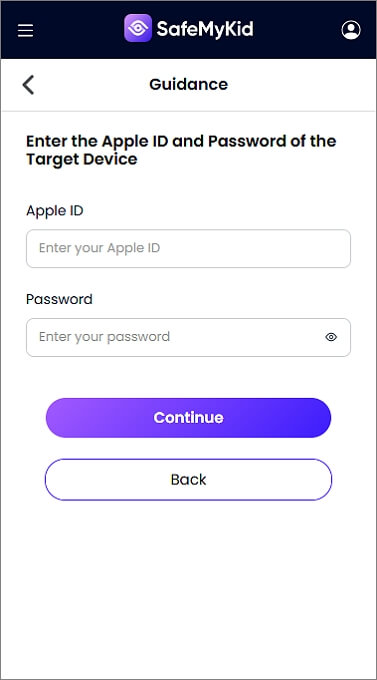
How to Use SafeMyKid Spyware on iPhone
Step 1. Sign up
Visit the SafeMyKid website and create an account.

Step 2. Input iCloud Details
Enter the target iPhone’s iCloud credentials to gain access to the device without installing any software.
Step 3. Start Spying on iPhone
After syncing with iCloud, you can begin monitoring the device’s activity directly from the web dashboard.

With these easy steps, you can start using SafeMyKid to monitor and protect your loved ones' mobile activities efficiently.
8 Common Ways to Install Spyware via Text Message
While there may be ways to manipulate a target phone through text messages, it is crucial to consider the ethical and legal aspects involved. Here, we'll explore various ways spyware can be potentially installed via text message.
1. Phishing Links in SMS

How It Works: Attackers send a text with a link disguised as something important—such as a bank notification, security update, or package delivery alert. Once clicked, spyware is secretly installed.
Scenario: A user receives a text from "Apple Security" saying, "Your iCloud has been compromised. Verify your account now: [malicious link]." Clicking the link downloads spyware that logs keystrokes and steals information.
Effectiveness: Works on both Android and iPhone if the user is tricked.
Warning: Using phishing links to deceive individuals and install spyware is illegal and unethical. It violates privacy rights and can lead to criminal charges, including identity theft, fraud, and data breaches.
2. Malicious APK Files (Android Only)

How It Works: Android allows users to install apps outside the Google Play Store. Attackers exploit this by sending an APK file through text and tricking the user into installing it.
Scenario: A user gets a message: "Install this app to see who viewed your WhatsApp profile." The APK file installs spyware instead.
Effectiveness: It works only on Android because iPhones restrict third-party installations.
Warning: Distributing malicious APK files to install spyware is a clear violation of digital privacy laws and can result in severe penalties. It is a form of cybercrime that can lead to criminal charges, including hacking and unauthorized access to personal information.
3. iMessage Exploits (iPhone Only)

How It Works: Certain versions of iOS have vulnerabilities that allow spyware to be installed via an iMessage, even without user interaction.
Scenario: A hacker sends an invisible exploit message to an iPhone, triggering a vulnerability that installs spyware automatically.
Effectiveness: It works only on iPhones, but Apple frequently patches these flaws.
Warning: Exploiting vulnerabilities in iMessage to install spyware without user consent is an illegal and unethical act. It breaches the device owner’s privacy and can result in serious legal consequences.
4. Remote Access Trojans (RATs)

How It Works: Attackers send a disguised RAT app via text, which, once installed, gives them full control over the target phone.
Scenario: A user downloads a "battery saver" app from a link in a text. It secretly installs a RAT, allowing hackers to access files, microphones, and locations.
Effectiveness: Works on both Android and iPhone if the target installs the app.
Warning: Installing RATs through disguised apps is a highly illegal activity. Such actions constitute cyber intrusion and can result in severe criminal charges, including hacking, surveillance, and invasion of privacy.
5. Fake App Updates via SMS

How It Works: A text message is sent claiming that a critical app update is necessary for the phone’s security or to improve functionality. The message typically includes a link to an unofficial website, where the user unknowingly installs spyware disguised as the update.
Scenario: A user receives a text message that says, "Urgent! A critical update for your WhatsApp is available. Click here to install now." After clicking the link, the user is redirected to a page that appears to be a legitimate update, but in reality, it installs spyware on the device.
Effectiveness: Works on both Android and iPhone if the user falls for it.
Warning: Sending fake app updates to install spyware is considered a deceptive and malicious activity. This is a violation of trust and can result in legal penalties, including charges for fraud and digital harassment.
6. Spyware in Multimedia Messages (MMS)
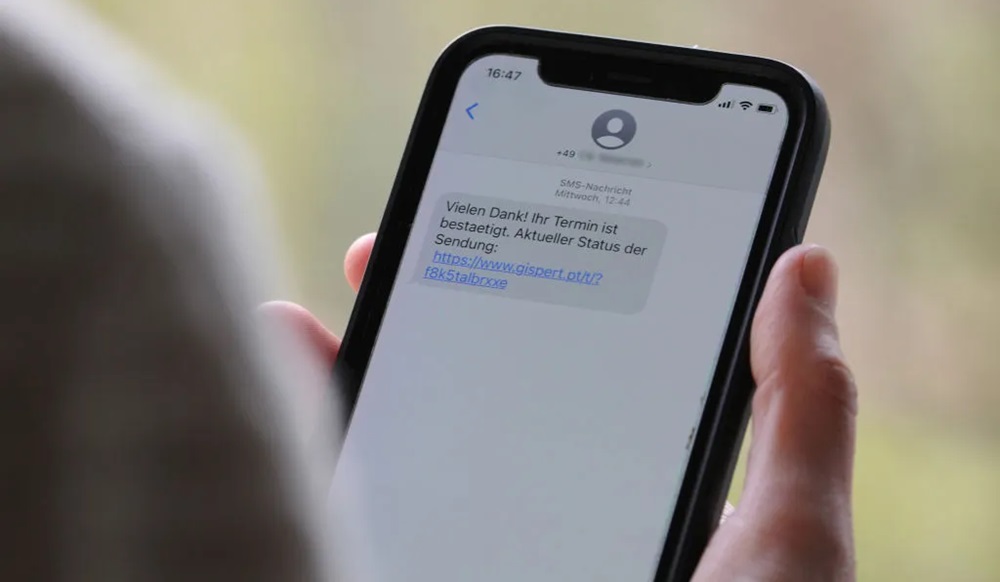
How It Works: Malware is embedded in an MMS attachment such as a photo, video, or voice note. When opened, it installs spyware on the device.
Scenario: A victim receives an MMS containing an enticing video or image. Once opened, the spyware is activated, silently tracking the phone’s activities.
Effectiveness: More common on Android, as iPhones restrict automatic MMS downloads.
Warning: Distributing malware through MMS attachments to install spyware is illegal. It can lead to criminal charges for distributing malicious software, invasion of privacy, and potential harm to the victim.
7. Social Engineering Traps
How It Works: Attackers impersonate trusted contacts to trick users into installing spyware.
Scenario: A user receives a message from “Mom”: “Hey, I need you to download this app to call me for free!” The app is spyware.
Effectiveness: Works on both platforms.
Warning: Using social engineering tactics to trick individuals into installing spyware is deceptive and unethical. It violates privacy and trust and is illegal in many jurisdictions.
8. Pre-Installed Spyware via Text Activation

How It Works: Some spyware is pre-installed and only needs a text command to activate.
Scenario: A message appears from “Mom,” saying, “Hey, I need you to download this app to call me for free!” The app is spyware.
Effectiveness: Rare, but possible.
Warning: Activating pre-installed spyware via text messages without consent is a violation of privacy rights. It is an illegal practice, and perpetrators can be prosecuted under laws related to unauthorized access, surveillance, and data theft.
How to Detect Spyware on Your Phone If You Suspect Someone Installed It

If you believe your phone may have been compromised by spyware, there are several indicators you should look out for. These signs can help you identify if malicious software is running on your device:
- Unusual Battery Drain: Spyware often operates in the background, using up your phone’s power. If you notice that your battery is draining faster than usual without heavy usage, spyware could be the cause.
- Increased Data Usage: Spyware frequently sends information from your device to the attacker, which can lead to higher-than-normal data consumption. If you’re suddenly using more data than usual, it's worth investigating further.
- Strange Text Messages: Some spyware programs communicate with the attacker via text messages that may appear as coded or jumbled symbols. If you receive mysterious texts that you didn't send or understand, this could be a red flag.
- Performance Issues: If your phone starts overheating or running slower than usual, especially when you're not using demanding apps, it might be due to spyware running secretly in the background.
- Unusual Background Noise or Calls: If you hear strange noises or your calls are interrupted unexpectedly, spyware might be using your phone's microphone to listen in on conversations.
- Pop-ups and Unwanted Ads: A significant increase in pop-ups, ads, or unfamiliar apps on your phone could signal the presence of spyware. These pop-ups can be used to track your activity or collect your personal information.
- Unfamiliar Apps or Settings: Check your installed apps by going to Settings > Apps > Manage Installed Apps. Look for any unfamiliar apps or settings that you didn’t intentionally install.
By keeping an eye out for these signs and taking proactive measures, you can protect your phone from being compromised by spyware.
FAQs on How to Install Spyware via Text Message Free
If you're considering using spyware installation via text messages, it's essential to understand the common questions and clarify misconceptions. Below are some frequently asked questions about installing spyware through text messages for free.
1. Can spyware installed via text message be removed from a phone?
Yes, spyware can be removed, but the process depends on the type of spyware. Here’s what you can do:
- For Android: Factory reset the device and reinstall apps manually.
- For iPhone: Update iOS to the latest version, as many spyware tools exploit security flaws that Apple frequently patches.
- For Both: Run a full malware scan using a security app like Malwarebytes or Norton Mobile Security.
2. Can I legally install spyware on someone’s phone?
Installing spyware on a phone without the owner’s consent is illegal in most countries. However, parents may use monitoring software like SafeMyKid to track their children's devices for safety purposes.
Employers may also monitor company-owned devices with proper disclosure. Always check local laws before using any spyware tool.
3. Do spyware apps work if the target phone is turned off?
No, spyware apps cannot function if the target phone is completely powered off. However, some advanced spyware can still store collected data and send it once the phone is turned back on.
If the phone has been compromised, shutting it down will temporarily stop the monitoring but won’t remove the spyware.
4. Can someone install spyware via text message without me clicking anything?
While most spyware requires user interaction (clicking a link, downloading an app), zero-click attacks exist but are rare. These exploit security flaws in apps like iMessage or WhatsApp, allowing spyware to be installed remotely without the user clicking anything.
Apple and Google frequently update their systems to patch such vulnerabilities, so keeping your device updated reduces this risk.
5. Will a factory reset completely remove all spyware?
Yes, a factory reset will remove most spyware applications, but advanced spyware that modifies the phone’s firmware may survive. If you suspect persistent spyware:
- For Android, reinstall the operating system using a PC.
- For the iPhone, restore the device using iTunes and set it up as a new phone instead of restoring from a backup.
Conclusion
There are multiple ways to install spyware via text message free, but most require some form of user interaction, such as clicking a link or downloading an app.
However, if you are looking for a legitimate, secure, and undetectable way to monitor a device, SafeMyKid is the best option. It provides reliable tracking and comprehensive monitoring.


