SIM Cloning: 5 Powerful Methods to Clone SIMs and 6 Ways to Keep Your SIM Safe

The rise of mobile banking and digital transactions has made SIM cloning a powerful tool—not just for cybercriminals but also for individuals who need to monitor phone activity responsibly.

In this guide, we’ll explore how SIM cloning works, the techniques used to clone SIM cards, and, most importantly, six effective ways to prevent unauthorized cloning.
What Is SIM Cloning?
SIM cloning is an advanced mobile technology that allows the duplication of a SIM card, enabling seamless access to phone calls, messages, and data from another device. While often associated with security risks, SIM cloning has legitimate uses for parents, employers, and businesses.
For parents, SIM cloning ensures they stay informed about their children’s digital interactions and safety. Employers can use it to monitor company-issued devices, ensuring compliance with workplace policies.

Additionally, professionals who manage multiple devices can benefit from SIM duplication for convenience and efficiency. By copying the International Mobile Subscriber Identity (IMSI) and authentication key, a cloned SIM functions as an exact replica of the original.
When used responsibly, SIM cloning can be a powerful tool for security, monitoring, and effective communication management.
Why You Might Want to Clone Someone’s SIM?

SIM cloning isn't just for hackers—it has legitimate, responsible uses that can benefit parents, employers, and individuals managing multiple devices. Here’s why you might consider cloning a SIM:
- Parental Monitoring for Child Safety
Parents can use SIM cloning to stay informed about their children’s digital activities, ensuring their safety online and offline. By monitoring calls, messages, and location, parents can protect their kids from cyberbullying, online predators, and other potential risks.
- Employee Monitoring & Business Security
Employers can clone company-issued SIM cards to track business-related calls and messages, ensuring employees follow company policies. This is especially useful for industries that handle sensitive data, logistics, or sales teams working remotely.
- Backup & Convenience for Multiple Devices
For professionals managing multiple phones, cloning a SIM allows seamless communication across all devices. Whether you need to access work-related calls on a secondary phone or travel frequently, SIM cloning helps streamline communication without needing multiple numbers.
- Elderly or Dependent Care
Caregivers of elderly family members or dependents can use SIM cloning to stay connected and ensure their loved ones receive important calls and messages. This is particularly useful for individuals with medical conditions who might need constant supervision.
- Recovering Lost or Damaged SIM Data
If a SIM card gets lost or damaged, cloning allows you to restore access to important contacts, messages, and network services quickly. This eliminates the hassle of getting a new SIM and waiting for a number transfer.
How Does SIM Cloning Work?
There are several ways to clone a SIM card, depending on the security features in place. Here are the five most common techniques:
1. Use SafeMyKid for SIM Cloning

SafeMyKid is a powerful tool that helps monitor SIM card activity, detect unauthorized changes, and alert users in real time.
With real-time alerts, call and message monitoring, and location tracking, SafeMyKid ensures complete oversight of a device’s activity while maintaining discretion.
Key Features of SafeMyKid SIM Cloner
With SafeMyKid, SIM cloning is not just about duplication—it’s about security, monitoring, and control for responsible users. Whether you’re a parent ensuring your child’s safety or a partner ensuring your spouse doesn’t cheat on you, SafeMyKid offers a seamless way to stay informed.
- Call and Message Logs:Gain full access to incoming and outgoing call records, including timestamps, contact details, and SMS conversations, directly from the cloned SIM.
- Multi-Device Support:Monitor multiple SIM cards across different devices from a single dashboard, making it an ideal solution for managing multiple users.
- Location Tracking: Track a phone’s location through the cloned SIM by using GPS technology.
- SIM Activity Alerts: Receive instant notifications for SIM card changes, number switches, or suspicious activity like unexpected network resets.
- Encrypted Remote Access: Access all SIM data securely from anywhere via an encrypted connection, ensuring your privacy and control are never compromised.
How to Set Up SafeMyKid to Clone SIMs
Setting up SafeMyKid for SIM cloning is quick and user-friendly, ensuring seamless monitoring without technical complexities. Follow the steps below to set up SafeMyKid.
How to Clone SIMs on Android Devices
Step 1. Sign Up
Create an account on SafeMyKid’s official website

Step 2. Install and Configure the Android App
Install SafeMyKid on the target device. Follow the on-screen instructions to enable SIM monitoring.
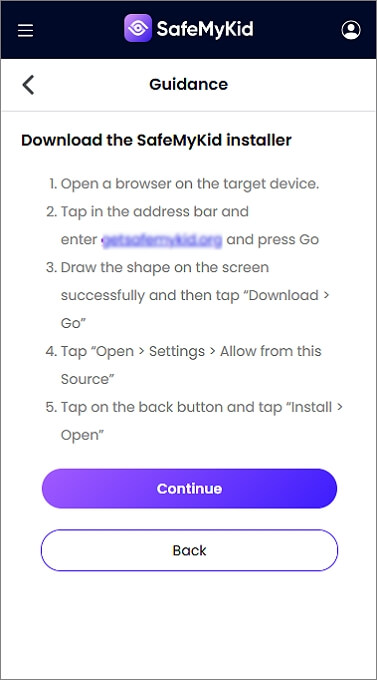
Step 3. Begin SIM Cloning on Android
Start monitoring SIM activity from your online dashboard.
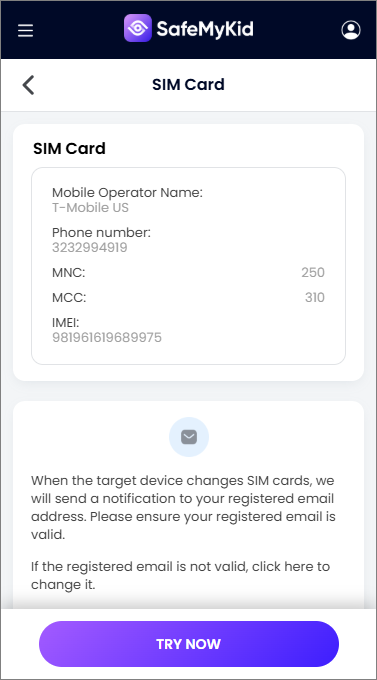
How to Clone SIMs on Apple Devices
Step 1. Sign Up
Register on SafeMyKid’s website using your email address.

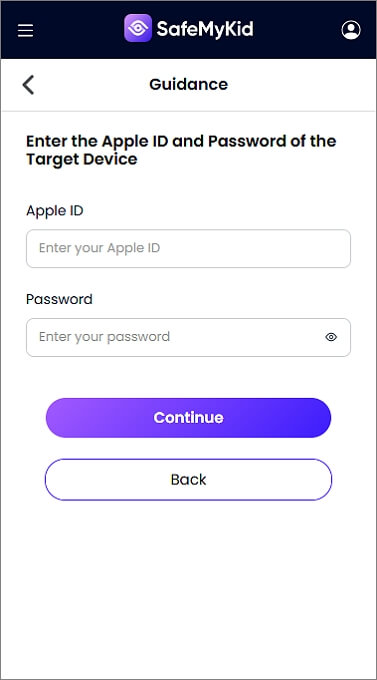
Step 2. Input iCloud Details
Enter the target device’s iCloud credentials (no app installation needed).
Step 3. Begin to Clone SIM on iPhone
Access SIM data remotely via your control panel.

SafeMyKid ensures real-time alerts and proactive SIM activity tracking, giving you peace of mind while staying informed.
2. Physical SIM Cloning
Physical SIM cloning involves copying a SIM card’s unique identifiers onto a blank SIM using specialized hardware. While often used maliciously, this technique can also help parents monitor their children’s calls or allow businesses to manage company-owned devices more efficiently.
How It Works:
- The SIM card is inserted into a cloning device or reader.
- The device extracts the International Mobile Subscriber Identity (IMSI) and authentication key.
- The data is written onto a blank SIM, creating an identical copy.
Best Use Case: Ideal for duplicating SIMs when managing multiple devices.
Limitation:
- Modern SIMs use strong encryption, making cloning more challenging.
3. Remote SIM Cloning (IMSI Catching)
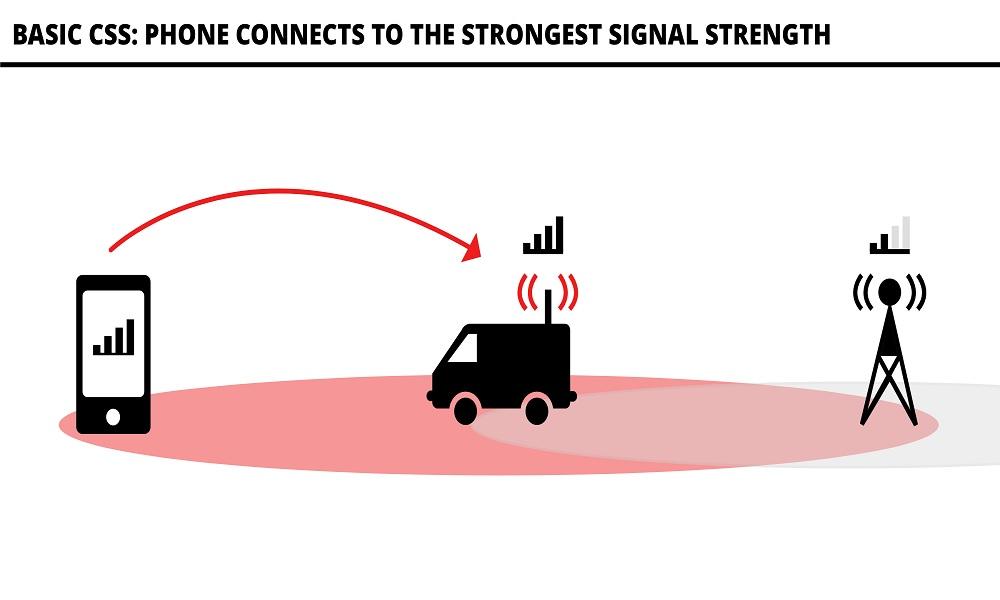
IMSI catching is an advanced technique used to duplicate a SIM card’s data remotely. While cybercriminals exploit it for unauthorized access, this method can also be used for security and surveillance purposes.
How It Works:
- A fake mobile tower (IMSI catcher) is set up near the target.
- The victim’s phone automatically connects to the rogue network.
- The attacker intercepts the SIM’s IMSI and authentication key.
Advantage:
- No physical access to the SIM is needed.
Limitation:
- Requires advanced equipment, making it less accessible.
4. Social Engineering or Insider Access
This is a social engineering attack where hackers convince your mobile carrier to transfer your phone number to a new SIM card under their control. It allows seamless access to call logs, messages, and mobile activities.
How It Works:
- The user provides the necessary identity details to the mobile carrier.
- A request is made to transfer the phone number to a new SIM.
- Once approved, the original SIM is deactivated, and the new one takes control.
Advantage:
- It works without requiring physical access to the target SIM.
Limitation:
- Some carriers require additional authentication to approve transfers.
5. SIM Card Duplication Via Software Tools
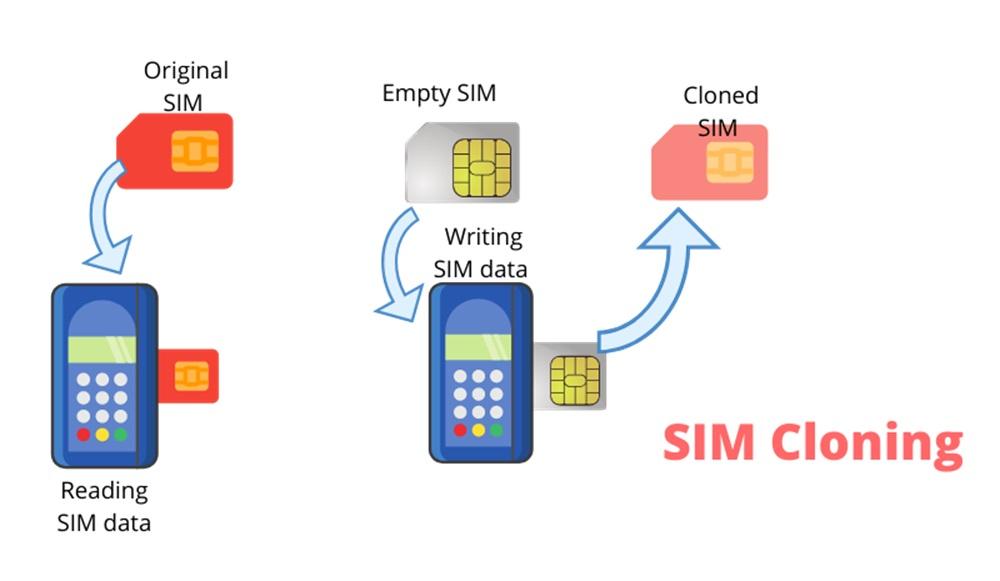
SIM card duplication using specialized software allows users to create a functional copy of a SIM card. This technique is commonly used for managing multiple devices on the same number, parental monitoring, or employee tracking.
How It Works:
- The original SIM card is inserted into a SIM reader connected to a computer.
- Specialized software extracts essential SIM data, including the IMSI and authentication key.
- The extracted data is written onto a blank SIM card, creating a duplicate.
- The cloned SIM can now be used in another device while retaining the same network identity.
Advantage:
- Allows seamless switching between multiple devices using the same number.
Limitation:
- Modern SIM cards use strong encryption, making duplication difficult.
6 Ways to Protect Yourself from SIM Cloning
While SIM cloning can be a valuable tool for monitoring, it’s essential to ensure that your own SIM remains protected from unauthorized duplication. Here are seven effective ways to safeguard your SIM card and mobile data:
1. Use Strong Account Security

One of the easiest ways to prevent SIM cloning is by securing your online and mobile carrier accounts. Hackers often gain access through weak passwords or lack of authentication measures.
- Set up multi-factor authentication (MFA) for all accounts.
- Use a strong, unique password for your mobile carrier account.
- Enable PIN or biometric authentication for SIM-related requests.
2. Beware of Phishing Scams

Most SIM cloning attempts begin with phishing attacks, where fraudsters trick you into revealing personal information.
- Never click on links in unsolicited emails or messages.
- Verify any communication claiming to be from your carrier.
- Never share your SIM details or OTP codes with anyone.
3. Contact Your Mobile Carrier for Extra Security

Many mobile networks offer security features that can help prevent unauthorized SIM swaps or clones.
- Enable a SIM swap PIN to prevent unauthorized changes.
- Set up real-time alerts for any changes to your account.
- Ask your carrier if they offer additional security measures.
4. Watch for Sudden Loss of Network Signal

A sudden loss of signal on your phone without explanation could mean your SIM has been cloned.
- Restart your phone to check if it reconnects.
- Insert your SIM into another phone to test network availability.
- Contact your mobile provider immediately if the issue persists.
5. Avoid Public USB Charging Stations
Some hackers use public charging stations to inject malware into phones, allowing them to extract SIM data.
- Always use your personal charger.
- Carry a power bank to avoid public charging stations.
- Use a USB data blocker to prevent unauthorized data transfers.
6. Monitor Your Bank and Online Accounts

Since SIM cloning can lead to financial fraud, keeping an eye on your transactions is crucial.
- Enable instant transaction alerts on your bank accounts.
- Regularly check your financial statements for unauthorized activity.
- Use additional authentication for online banking.
FAQs on SIM Cloning
Understanding SIM cloning can help you make informed decisions about monitoring and security. Here are some commonly asked questions:
1. Can SIM cloning be detected by the mobile carrier?
Yes, mobile carriers have systems in place to detect suspicious SIM activity. Many networks can flag unusual changes, such as multiple SIM registrations with the same number or abrupt changes in location and device.
However, these security measures are not foolproof, and in some cases, hackers can bypass detection using advanced cloning techniques.
2. Does airplane mode protect against SIM cloning?
No, airplane mode does not prevent SIM cloning. If a hacker has already cloned your SIM, switching to airplane mode only disables your network temporarily, but it does not stop the cloned SIM from functioning.
3. Can a cloned SIM card be used in a different country?
Yes, a cloned SIM card can work in a different country, depending on the fraudster's method. If the hacker clones your SIM without alerting your mobile carrier, the duplicate can function normally on any network that supports international roaming.
4. Can hackers listen to my phone calls if my SIM is cloned?
Yes, if a hacker successfully clones your SIM, they can intercept and listen to phone calls made to your number. Since both your original and cloned SIM share the same number, calls and messages can be received by both devices simultaneously in some cases.
5. Is SIM cloning more common with prepaid or postpaid SIM cards?
Both prepaid and postpaid SIMs can be cloned, but postpaid SIMs are often more targeted because they are linked to financial transactions, credit accounts, and banking services.
6. Can I still use my phone if my SIM is cloned?
Yes, but your network connection may be disrupted. In many cases, when a hacker activates a cloned SIM, your original SIM may stop receiving calls and messages.
If you suddenly experience:
- No service or signal loss without reason
- Missed calls despite having full network bars
- Unusual text messages about SIM-related changes
Then your SIM may have been cloned, and you should contact your mobile provider immediately.
Conclusion
With the right approach, SIM cloning can be used responsibly for security and oversight. If you’re looking for a way to clone a SIM card, consider using SafeMyKid.
SafeMyKid offers more features like call and SMS tracking, location tracking, social media monitoring, and lots more! Try SafeMyKid today.